Amplitude Shift Keying is one of the digital modulation techniques in digital communication.
Passband transmission: In this approach, the digital data is modulated with a high-frequency carrier signal. It is suitable for long-distance transmission.
Modulation Techniques:
1. Amplitude Shift Keying(ASK)
2. Frequency Shift Keying(FSK)
3. Phase Shift Keying(PSK)
Table of Contents
Types of Detector/Demodulators:
These are 2 types(based on carrier signal)
1. Coherent detector/synchronous detector
2. Non-coherent detector/Analog detector
Coherent detector: The carrier signal at the transmitter and receiver must be in the same phase.
Non-coherent detector: The carrier signal at the transmitter and receiver may not be in the same phase.
Amplitude shift keying is also called on/off key.
It is the simplest modulation technique
Basic digital modulation: The amplitude of the analog carrier undergoes direct modulation by a binary signal. There are only two potential output amplitudes, and ASK is also known as digital amplitude modulation (DAM).
1-ON state
0-OFF state
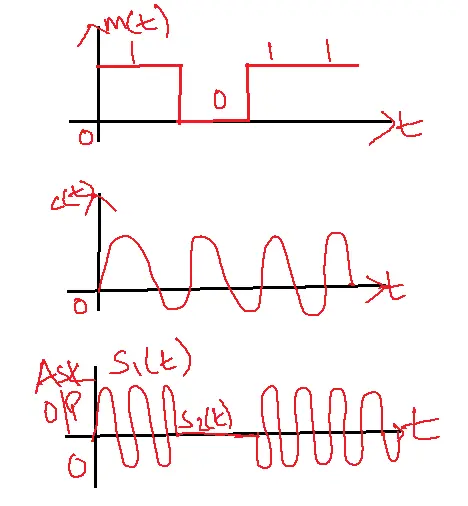
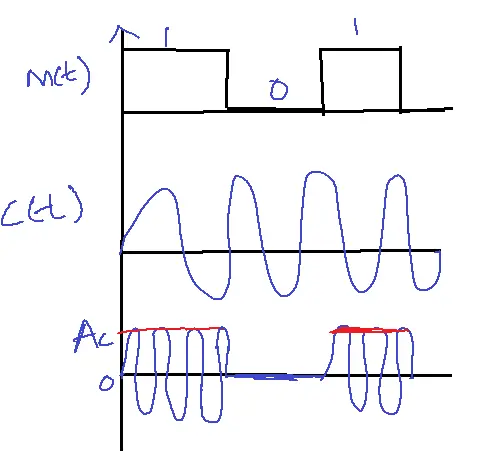
Amplitude Shift Keying Generator:
Let m(t) be the message signal,
c(t) is the carrier signal.
c(t)-Accos2πfct
then s(t)=m(t) x c(t)
s(t)=c(t) if m(t)=1
s1(t)= Accos2πfct
s2(t)=0
P=Ac2/2
Amplitude Shift Keying coherent detector:
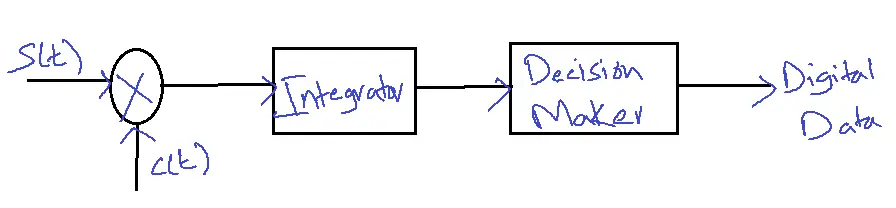
Case-I: s(t)=s1(t)
P(t)= s1(t) x c(t)
= Accos2πfct x Accos2πfct
=Ac2[1+cos2πfct/2]
P(t)= s1(t) x c(t)
= Ac2/2 + Ac2/2 cos2πfct
Output= Ac2/2
Case-2: s(t)= s2(t)
The product of the integrator is zero. [constant value]
s2(t)=0
P(t)=0
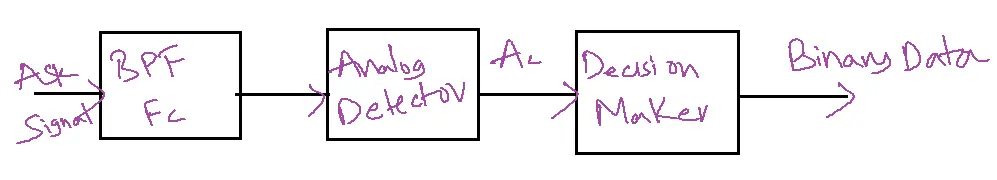
Amplitude Shift Keying Non-coherent detector/Analog Detector:
Power spectral density and Bandwidth of ASK:
fB-Bit frequency
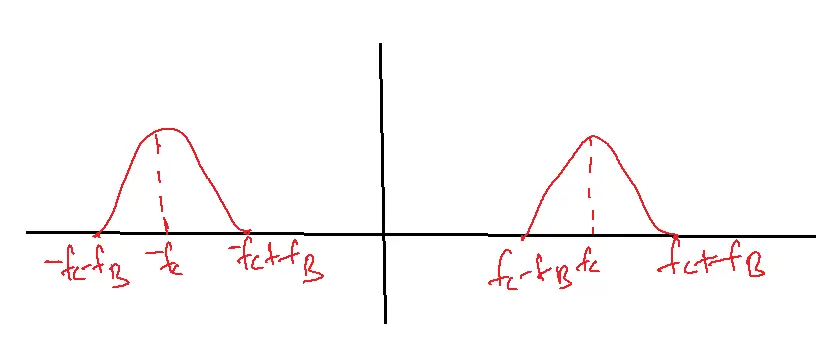
Bandwidth of ASK=2fB
Probability of error in ASK:
S1(t)= Accos2πfct
S2(t)=0
Pe=( A1-A2)2
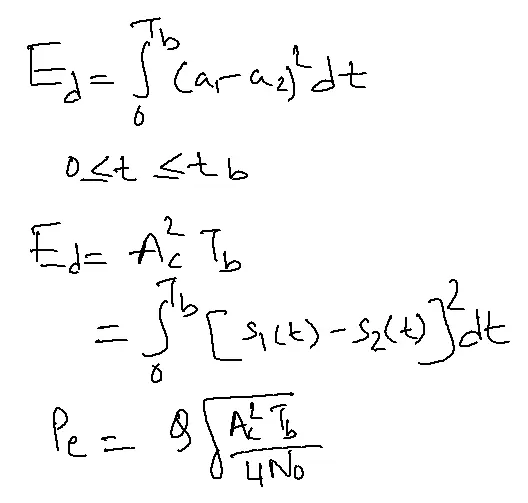
Advantages of ASK:
1. Simple Implementation: ASK is a straightforward modulation technique, easy to implement and understand, making it a great choice for beginners.
2. Cost-Effective: ASK requires minimal hardware and software, reducing costs and making it an attractive option for businesses.
3. Low Power Consumption: ASK signals require less power to transmit, making them suitable for battery-powered devices and reducing energy costs.
4. Easy Demodulation: ASK signals can be demodulated using simple envelope detectors, streamlining the process.
5. Compatibility: ASK is compatible with existing communication systems and infrastructure, ensuring seamless integration.
Disadvantages of ASK:
1. Noise Susceptibility: ASK signals are vulnerable to noise and interference, which can cause errors in data transmission and impact reliability.
2. Limited Bandwidth Efficiency: ASK has a relatively low bandwidth efficiency, making it less suitable for high-speed data transmission and large data transfers.
3. Multipath Disruption: ASK signals can be disrupted by multipath propagation, leading to signal fading and distortion, and impacting performance.
4. Security Risks: ASK signals can be easily intercepted and decoded, making them less secure than other modulation techniques and data at risk.
5. Frequency Limitations: ASK is not applicable for high-frequency applications due to its limited bandwidth and susceptibility to noise, restricting its use in certain industries.
Applications of ASK:
1. Radio Communication: ASK is used in radio communication systems, such as amplitude-modulated (AM) radios, to transmit audio signals.
2. Computer Networks: ASK is used in local area networks (LANs) and wide area networks (WANs) to transmit data over cable or wireless connections.
3. Satellite Communication: ASK is used in satellite communication systems for transmitting data between satellites and ground stations.
4. Optical Communication: ASK is used in optical fiber communication systems to transmit data as light signals.
5. IoT Devices: ASK is used in some Internet of Things (IoT) devices, such as remote sensors and actuators, due to its simplicity and low power consumption.
6. Wireless Sensor Networks: ASK is used in wireless sensor networks (WSNs) for data transmission between sensor nodes.
7. Digital Signaling: Digital signaling systems, particularly in the realms of alarms and remote controls, utilize Amplitude Shift Keying (ASK) for data communication.
8. Power Line Communication: ASK is used in power line communication systems to transmit data over power lines.
These applications take advantage of ASK’s simplicity, low cost, and ease of implementation, making it a widely used modulation technique in various fields.
FAQs of Related Topic:
1. What is Amplitude Shift Keying (ASK)?
- ASK is a digital modulation technique where the amplitude of a carrier wave is varied to represent digital data.
- It’s a simple form of modulation used in various communication systems.
2. How does Amplitude Shift Keying (ASK) work?
- In ASK, the carrier wave’s amplitude is switched between two or more levels to represent binary 1s and 0s.
- A higher amplitude typically represents a ‘1’, while a lower or zero amplitude represents a ‘0’.
3. What are the applications of ASK?
ASK is commonly used in:
- Wireless communication systems: keyless entry systems, remote controls, and RFID tags.
- Optical fiber communication: For transmitting digital data over long distances.
- Low-cost, short-range communication: Simplicity and cost-effectiveness are more important than high data rates.
4. What are the advantages and disadvantages of ASK?
Advantages:
- Simple implementation and demodulation
- Cost-effective
Disadvantages:
- Susceptible to noise and interference
- Less power efficient compared to other modulation schemes
- Limited data transmission rate
5. What are the different types of ASK?
The main types of ASK are:
- On-Off Keying (OOK): The carrier is either fully on or off.
- Binary ASK (BASK): Two amplitude levels represent binary data.
- Multilevel ASK (MASK): Multiple amplitude levels enable the transmission of multiple bits per symbol.
